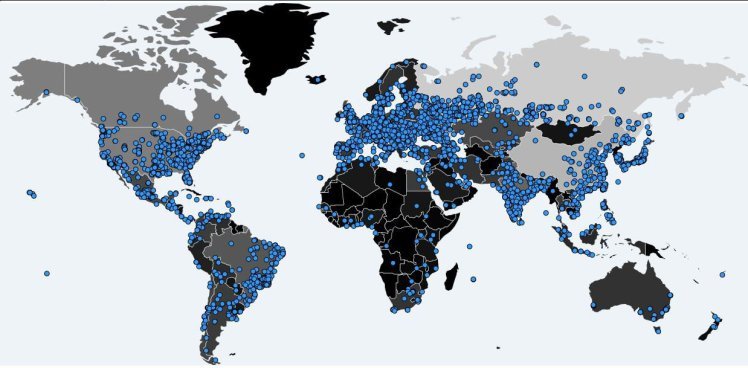
A global cyber-attack using hacking tools believed to have been created by the US National Security Agency (NSA) has infected tens of thousands of computers in nearly 100 countries.
Cyber-extortionists on Friday tricked victims into opening malicious malware attachments to spam emails that appeared to contain invoices, job offers, security warnings, and other legitimate files.
The ransomware then encrypted data on the computers, demanding payments of $300-$600 to restore access. Security researchers said they observed some victims paying via the digital currency bitcoin, though they did not know what percent had given in to the digital extortionists.
Researchers with security software maker Avast said they had observed 57,000 infections in 99 countries with Russia, Ukraine, and Taiwan the top targets.
The most disruptive attacks were reported in Britain, where hospitals and clinics were forced to turn away patients after losing access to computers.
“We are experiencing a major IT disruption and there are delays at all of our hospitals,” said the Barts Health group, which manages major London hospitals. Routine appointments had been cancelled and ambulances were being diverted to neighbouring hospitals.
International shipper FedEx Corp said some of its Windows computers were also infected
James Scott, from the Washington DC-based Institute of Critical Infrastructure Technology, said ransomware emerged “as an epidemic” in 2016. He said the healthcare sector was particularly vulnerable because of poor digital security knowledge.
“The staff have no cyber-hygiene training, they click on phishing links all the time. The sad thing is they weren’t backing up their data properly either, so that’s a big problem. They should be doing that all the time,” Scott told Al Jazeera.
“Everyone’s vulnerable right now because you’re only as strong as your weakest link within your organisation from a cyber-perspective.”
Hackers appear to have begun the campaign by targeting organisations in Europe, said Vikram Thakur, research manager with security software maker Symantec.
By the time they turned their attention to the United States, spam filters had identified the new threat and flagged the ransomware-laden emails as malicious, Thakur said.
Private security firms identified the ransomware as a new variant of “WannaCry”, which has the ability to automatically spread across large networks by exploiting a known bug in Microsoft’s Windows operating system.
“Once it gets in and starts moving across the infrastructure, there is no way to stop it,” said Adam Meyers, a researcher with cyber-security firm CrowdStrike.
The hackers, who have not come forward to claim responsibility or otherwise been identified, likely made it a “worm”, or self-spreading malware, by exploiting a piece of NSA code known as “Eternal Blue”, which was released last month by a group known as the Shadow Brokers, researchers with several private cyber-security firms said.
“This is one of the largest global ransomware attacks the cyber-community has ever seen,” said Rich Barger, director of threat research with Splunk, one of the firms that linked WannaCry to the NSA.
The Shadow Brokers released Eternal Blue as part of a trove of hacking tools that they said belonged to the US spy agency.
On Friday, Russia’s interior and emergencies ministries, as well as the country’s biggest bank, Sberbank, said they were targeted. The interior ministry said on its website about 1,000 computers had been infected but it had localised the virus.
Although cyber-extortion cases have been rising for several years, they have to date affected small-to-mid-sized organisations, disrupting services provided by hospitals, police departments, public transportation systems and utilities in the United States and Europe.
The news is also likely to embolden cyber-extortionists when selecting targets, Chris Camacho, chief strategy officer with cyber intelligence firm Flashpoint, said.
“Now that the cyber criminals know they can hit the big guys, they will start to target big corporations. And some of them may not be well prepared for such attacks,” Camacho said.